WordPress Google Fonts Plugin Vulnerability Affects Up To +300,000 Sites
- Digital MarketingNews
- January 8, 2024
- No Comment
- 140
[ad_1]
A vulnerability rated as Excessive was not too long ago patched in a Google Fonts optimization plugin for WordPress, permitting attackers to delete complete directories and add malicious scripts.
OMGF | GDPR/DSGVO Compliant WordPress Plugin
The plugin, OMGF | GDPR/DSGVO Compliant, Sooner Google Fonts. Simple., optimizes using Google Fonts to cut back web page pace impression and can also be GDPR compliant, making it helpful for customers within the European Union seeking to implement Google Fonts.
Screenshot of Wordfence Vulnerability Score
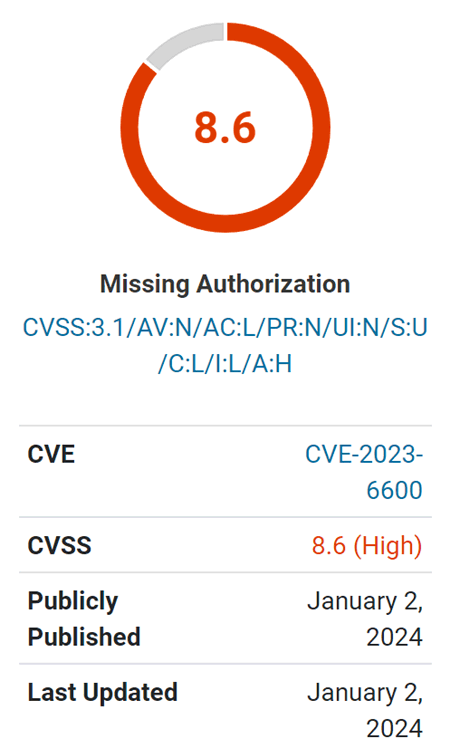
Vulnerability
The vulnerability is especially regarding as a result of it permits unauthenticated attackers. “Unauthenticated” implies that an attacker doesn’t have to be registered on the web site or have any stage of credentials.
The vulnerability is described as enabling unauthenticated listing deletion and permitting the add of Cross-Website Scripting (XSS) payloads.
Cross-Website Scripting (XSS) is a kind of assault the place a malicious script is uploaded to a web site server, which might then be used to remotely assault the browsers of any guests. This can lead to accessing a consumer’s cookies or session info, enabling the attacker to imagine the privilege stage of that consumer visiting the location.
The reason for the vulnerability, as recognized by Wordfence researchers, is a scarcity of a functionality verify – a safety function that checks whether or not a consumer has entry to a particular function of a plugin, on this case, an admin-level function.
See additionally: WordPress Security: 16 Steps to Secure & Protect Your Site
An official WordPress developer page for plugin makers says this about functionality checking:
“Person capabilities are the precise permissions that you just assign to every consumer or to a Person function.
For instance, Directors have the “manage_options” functionality which permits them to view, edit and save choices for the web site. Editors then again lack this functionality which is able to stop them from interacting with choices.
These capabilities are then checked at numerous factors throughout the Admin. Relying on the capabilities assigned to a task; menus, performance, and different facets of the WordPress expertise could also be added or eliminated.
As you construct a plugin, ensure that to run your code solely when the present consumer has the required capabilities.”
Wordfence describes the reason for the vulnerability:
“…is weak to unauthorized modification of knowledge and Saved Cross-Website Scripting because of a lacking functionality verify on the update_settings() perform hooked through admin_init in all variations as much as, and together with, 5.7.9.”
Wordfence additionally states that earlier updates tried to shut the safety hole however considers model 5.7.10 to be essentially the most safe model of the plugin.
Learn the Wordfence vulnerability warning:
Featured Picture by Shutterstock/Nikulina Tatiana
[ad_2]
Source link